Forty-two million records of Telegram users have been exposed online via an unprotected database.
The data remained online and accessible for at least 11 days before the host took them down.
You can follow this link to see if your information has leaked. link address
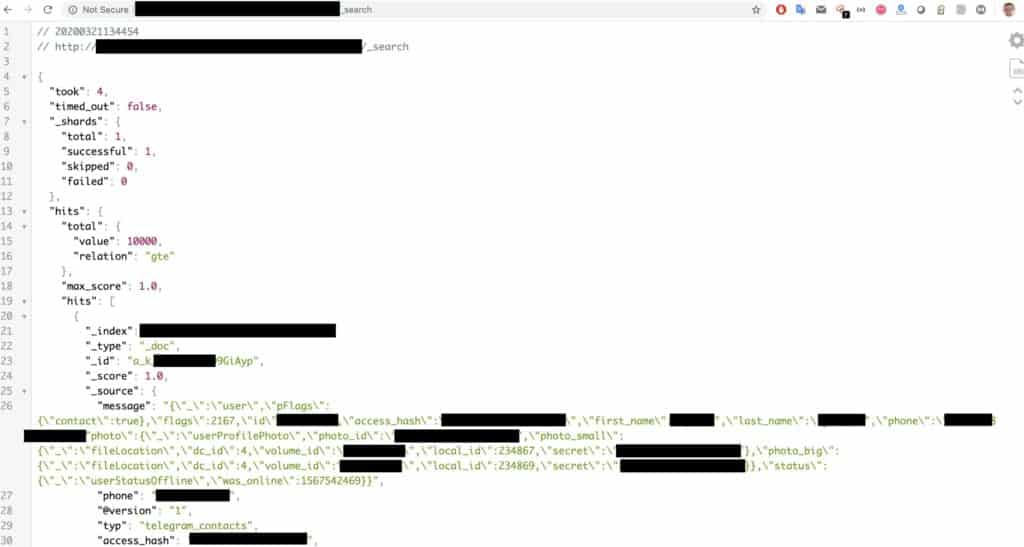
A fork messaging app that was derived from the Telegram source code has leaked 42 million records belonging to Asian.The discovery was the work of researcher Bob Diachenko, who found the database online and accessible without any password protection. Each database entry contained the username (Telegram ID), the corresponding phone number, hashes, and secret keys. The owner of the database and uploader of the data had the name “Hunting System,” which is not affiliated with the official Telegram entity. As the owner would never respond, Diachenko notified the hosting provider, and the Elasticsearch cluster was deleted.
一个从Telegram源码中衍生出来的Fork消息应用泄露了4200万条属于亚洲人的记录,这一发现是研究人员Bob Diachenko的工作,他发现这个数据库在线上可以在没有任何密码保护的情况下访问。每个数据库条目都包含了用户名(Telegram ID)、相应的电话号码、散列和密匙。数据库的所有者和数据上传者的名字是 "狩猎系统",与Telegram官方实体没有任何关系。由于该所有者永远不会回应,Diachenko通知了主机提供商,Elasticsearch集群被删除。
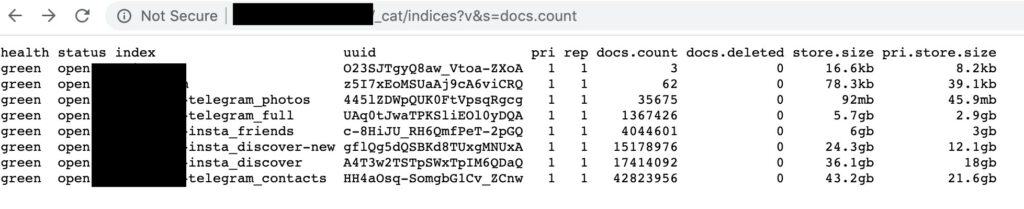
The date of the discovery is March 15, 2020, while the deletion of the cluster came 11 days later. It means that the 42 million records remained accessible to anyone with a Web browser for a significant period. As for the implications that resulted, for starters, the leak revealed the identities of those using Telegram (or a Telegram fork). In countries like Iran, this alone should be a reason for concern. Secondly, the exposed individuals are now at risk of getting SIM-swapped, and eventually, have their Telegram account taken over. Thirdly, phishing, and scamming via SMS is always a possibility too.
发现的日期是2020年3月15日,而删除该集群的时间是在11天后。这意味着,这4200万条记录在相当长的一段时间内,任何拥有网络浏览器的人都可以访问。至于由此产生的影响,首先,这次泄密暴露了使用Telegram(或Telegram fork)的人的身份。在伊朗这样的国家,光是这一点就应该引起人们的关注。其次,被曝光的人现在有可能会被换SIM卡,最终被盗用Telegram账户。第三,网络钓鱼和通过短信进行诈骗也总是有可能发生。
One explanation for this leak could be the negligence of the operators of the particular Telegram fork. Another answer could be the compromise of the data of this fork by the Iranian authorities, which could be “hunting” for Telegram users in the country. A third scenario, however, could link the app indirectly with the authorities, making it their creation. Remember, open-source code is available to anyone and not to a selection of ethical individuals, so anyone can create a Telegram fork and promote it to the users as trustworthy. The name “Hunting System” is one to get the cogs of conspiracy theorists turning for sure.
对于这种泄漏的一种解释可能是某个Telegram第三方应用的操作员疏忽。另一个可能是伊朗当局合作方开发的应用,这可能是在“寻找”该国的电报用户。第三种情况可能是与当局有某种间接关联,从而成为当局搜集用户的工具。请记住,任何人都可以使用开源代码,因此任何人都可以创建Telegram第三方应用并将其推广给用户。
你可以点击这个链接查询你的消息是否泄露